
OpenSSH is a 100% complete SSH protocol 2.0 implementation and includes sftp client and server support. OpenSSH also includes transitional support for the legacy SSH 1.3 and 1.5 protocols that may be enabled at compile-time. UPDATE -We have updated ssh-shellhost.exe binary (fix for #1222) in V7.7.2.0 payload on 8/4/2018. This release includes. Support for auto updating knownhosts via ssh and ssh-keygen; Optimized group membership resolution that results in vast performance improvement in processing simple user/group configuration rules. I have a Red Hat Enterprise Linux server (7.5 x8664). I have OpenSSH version 7.4. I was asked to upgrade it to a later version for security reasons: Nessus states that OpenSSH should be ugraded from 7.4 to 7.6 or later.However the Red Hat software and downloads does not have the latest package RPM. To upgrade openssh from 7.6 to 8.0 on Ubuntu 18.04 (bionic), I followed the instructions given here: How to Install OpenSSH 8.0 Server from Source in Linux. The version I started with: $ ssh -V OpenSSH7.6p1 Ubuntu-4ubuntu0.3, OpenSSL 1.0.2n 7 Dec 2017 Here are the commands to upgrade.
Openssh 7.9 Cve
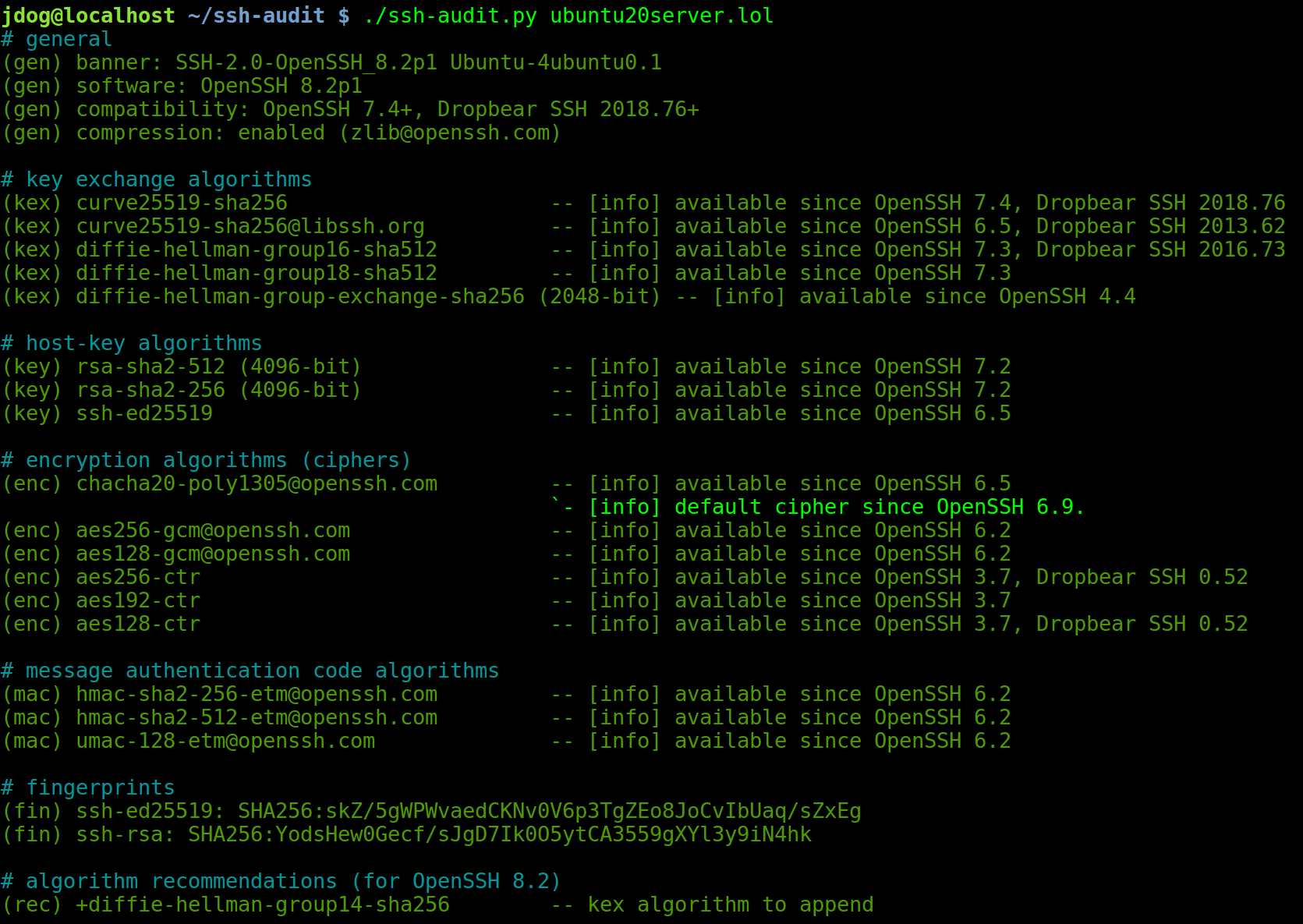
Openssh 7.9 Vulnerability
- OpenSSH_7.4p1 Debian-10+deb9u6, OpenSSL 1.0.2r 26 Feb 2019
- debug1: Reading configuration data /var/taroff/.ssh/config
- debug1: Reading configuration data /etc/ssh/ssh_config
- debug1: /etc/ssh/ssh_config line 19: Applying options for *
- debug2: ssh_connect_direct: needpriv 0
- debug1: Connection established.
- debug1: identity file /var/taroff/.ssh/id_rsa type 1
- debug1: key_load_public: No such file or directory
- debug1: identity file /var/taroff/.ssh/id_rsa-cert type -1
- debug1: key_load_public: No such file or directory
- debug1: identity file /var/taroff/.ssh/id_dsa type -1
- debug1: key_load_public: No such file or directory
- debug1: identity file /var/taroff/.ssh/id_dsa-cert type -1
- debug1: key_load_public: No such file or directory
- debug1: identity file /var/taroff/.ssh/id_ecdsa type -1
- debug1: key_load_public: No such file or directory
- debug1: identity file /var/taroff/.ssh/id_ecdsa-cert type -1
- debug1: key_load_public: No such file or directory
- debug1: identity file /var/taroff/.ssh/id_ed25519 type -1
- debug1: key_load_public: No such file or directory
- debug1: identity file /var/taroff/.ssh/id_ed25519-cert type -1
- debug1: Enabling compatibility mode for protocol 2.0
- debug1: Local version string SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u6
- debug1: Remote protocol version 2.0, remote software version OpenSSH_7.4p1 Debian-10+deb9u6
- debug1: match: OpenSSH_7.4p1 Debian-10+deb9u6 pat OpenSSH* compat 0x04000000
- debug1: Authenticating to s4:22 as 'taroff'
- debug3: hostkeys_foreach: reading file '/var/taroff/.ssh/known_hosts'
- debug3: record_hostkey: found key type ECDSA in file /var/taroff/.ssh/known_hosts:8
- debug3: order_hostkeyalgs: prefer hostkeyalgs: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521
- debug1: SSH2_MSG_KEXINIT sent
- debug1: SSH2_MSG_KEXINIT received
- debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,ext-info-c
- debug2: host key algorithms: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519-cert-v01@openssh.com,ssh-rsa-cert-v01@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256,ssh-rsa
- debug2: ciphers ctos: aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,ae.com,aes256-gcm@openssh.com,ae
- debug2: ciphers stoc: aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,ae.com,aes256-gcm@openssh.com,ae
- debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
- debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
- debug2: compression ctos: none,zlib@openssh.com,zlib
- debug2: compression stoc: none,zlib@openssh.com,zlib
- debug2: languages stoc:
- debug2: reserved 0
- debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1
- debug2: host key algorithms: ssh-rsa,rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519
- debug2: ciphers ctos: aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.comssh.com,aes256-gcm@openssh.com
- debug2: ciphers stoc: aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.comssh.com,aes256-gcm@openssh.com
- debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
- debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
- debug2: compression stoc: none,zlib@openssh.com
- debug2: languages stoc:
- debug2: reserved 0
- debug1: kex: host key algorithm: ecdsa-sha2-nistp256
- debug1: kex: server->client cipher: aes128-ctr MAC: umac-64-etm@openssh.com compression: none
- debug1: kex: client->server cipher: aes128-ctr MAC: umac-64-etm@openssh.com compression: none
- debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
- debug1: Server host key: ecdsa-sha2-nistp256 SHA256:6VAlx+MKEfh0HAvM0+4nflt2wcwxvXwJwIchiiltCvE
- debug3: hostkeys_foreach: reading file '/var/taroff/.ssh/known_hosts'
- debug3: record_hostkey: found key type ECDSA in file /var/taroff/.ssh/known_hosts:8
- debug3: hostkeys_foreach: reading file '/var/taroff/.ssh/known_hosts'
- debug3: record_hostkey: found key type ECDSA in file /var/taroff/.ssh/known_hosts:9
- debug3: load_hostkeys: loaded 1 keys from 192.168.0.4
- debug1: Host 's4' is known and matches the ECDSA host key.
- debug1: Found key in /var/taroff/.ssh/known_hosts:8
- debug2: set_newkeys: mode 1
- debug1: SSH2_MSG_NEWKEYS sent
- debug3: receive packet: type 21
- debug2: set_newkeys: mode 0
- debug2: key: /var/taroff/.ssh/id_rsa (0x561bbc352eb0)
- debug2: key: /var/taroff/.ssh/id_ecdsa ((nil))
- debug3: send packet: type 5
- debug1: SSH2_MSG_EXT_INFO received
- debug1: kex_input_ext_info: server-sig-algs=<ssh-ed25519,ssh-rsa,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521>
- debug2: service_accept: ssh-userauth
- debug3: send packet: type 50
- debug1: Authentications that can continue: publickey,password
- debug3: start over, passed a different list publickey,password
- debug3: preferred gssapi-keyex,gssapi-with-mic,publickey,keyboard-interactive,password
- debug3: remaining preferred: keyboard-interactive,password
- debug1: Next authentication method: publickey
- debug1: Offering RSA public key: /var/taroff/.ssh/id_rsa
- debug3: send packet: type 50
- debug2: we sent a publickey packet, wait for reply
- debug1: Server accepts key: pkalg ssh-rsa blen 279
- debug2: input_userauth_pk_ok: fp SHA256:sXMqmJgVBjQuZym233A9lET5NL7SBVv5MzWoNZFCaj4
- debug3: sign_and_send_pubkey: RSA SHA256:sXMqmJgVBjQuZym233A9lET5NL7SBVv5MzWoNZFCaj4
- debug3: receive packet: type 53
- 'System is booting up. See pam_nologin(8)'
Openssh 7.9p1 Rpm
